\/\The Conscience of a Hacker/\/
by
+++The Mentor+++
Written on January 8, 1986
=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
Another one got caught today,
it's all over the papers.
"Teenager Arrested in Computer Crime Scandal",
"Hacker Arrested after Bank Tampering"...
Damn kids. They're all alike.
But did you, in your three-piece psychology
and 1950's technobrain,
ever take a look behind the eyes of the hacker?
Did you ever wonder what
made him tick, what forces shaped him,
what may have molded him?
I am a hacker, enter my world...
Mine is a world that begins with school...
I'm smarter than most of
the other kids,
this crap they teach us bores me...
Damn underachiever. They're all alike.
I'm in junior high or high school.
I've listened to teachers explain
for the fifteenth time how to reduce a fraction.
I understand it.
"No, Ms. Smith, I didn't show my work.
I did it in my head..."
Damn kid. Probably copied it.
They're all alike.
I made a discovery today.
I found a computer.
Wait a second, this is cool.
It does what I want it to.
If it makes a mistake,
it's because I screwed it up.
Not because it doesn't like me...
Or feels threatened by me...
Or thinks I'm a smart ass...
Or doesn't like teaching
and shouldn't be here...
Damn kid. All he does is play games.
They're all alike.
And then it happened...
a door opened to a world...
rushing through the phone line
like heroin through an addict's veins,
an electronic pulse is sent out,
a refuge from
the day-to-day incompetencies is sought...
a board is found.
"This is it... this is where I belong..."
I know everyone here...
even if I've never met them,
never talked to them,
may never hear from them again...
I know you all...
Damn kid. Tying up the phone line again.
They're all alike...
You bet your ass we're all alike...
we've been spoon-fed baby food at
school when we hungered for steak...
the bits of meat that you did let slip
through were pre-chewed and tasteless.
We've been dominated by sadists, or
ignored by the apathetic.
The few that had something to teach
found us willing pupils,
but those few are like drops of water in the desert.
This is our world now...
the world of the electron and the switch,
the beauty of the baud.
We make use of a service
already existing without paying
for what could be dirt-cheap
if it wasn't run by profiteering gluttons,
and you call us criminals.
We explore... and you call us criminals.
We seek after knowledge... and you call us criminals.
We exist without skin color,
without nationality, without religious bias...
and you call us criminals.
You build atomic bombs, you wage wars,
you murder, cheat, and lie to us
and try to make us believe it's for our own good,
yet we're the criminals.
Yes, I am a criminal.
My crime is that of curiosity.
My crime is that of judging people
by what they say and think,
not what they look like.
My crime is that of outsmarting you,
something that you will never forgive me for.
I am a hacker,
and this is my manifesto.
You may stop this individual,
but you can't stop us all...
after all, we're all alike.
+++The Mentor+++
_______________________________________________________________________________
Original post
Friday, November 30, 2007
The Conscience of a Hacker
Thursday, November 29, 2007
The power of google

This post is being written after a long time since the previous one. Because of lack of time and mood. But this one is definitely one of the most important.
The most powerful search engine of the world- Google.com is indeed powerful. But, like every power, Google is also a double edged sword.
The search engine can be used to reveal password files of various sites, most of which are encrypted by the DES algorithm, and can be cracked right away. This will give access to various ftp servers, and who knows? may be even many telnet servers, or proxy servers of the corresponding sites.
In this post, I'll tell about the various search techniques in Google, which also work in many other search engines.
inurl (also allinurl) - This keyword is used to search for a specific string in the url(Uniform Resource Locator) of the sites being searched. Those with a positive match are listed in the search results.
for example,
inurl:google.com
will list all results, which have google.com in the url.
site - This keyword is used to search for a specific kind of site. Type of site is specified by the extension of the site. It may be .edu(Educational institution), .com(Commercial organization), .org(non profit organization), .gov(Governmental organization), .net(Network), .mil(Millitary network) and the others are normally country abbreviations(e.g. .jp for Japan, .in for India, .br for Britain etc.)
for example,
site:mil
will list all sites, with mil extension. This one is actually a U.S. millitary network.
filetype - This keyword is used to access certain file extensions in sites. This one is particularly useful for accessing password files. The password files are normally in the pwd, pw, mdb, xls extensions. The pwd files will store maintenance or service passwords.
for example,
filetype:mpg
will search for mpeg video files in the sites being searched. Other extensions can be searched in this way.
index of - This keyword is used to search for directory listings. It is also useful for searching certain types of files. It is particularly useful, if it is known, which directory, a certain type of file is stored in a web server. For example, the _vti_pvt folder will store service.pwd, which happens to store the service passwords.
for example,
index of /
will search for the directory listing of vulnerable sites.
OR - An uppercase OR acts as logical OR
intitle (also allintitle) - The intitle keyword is used to search for pages, which have the specified string in the title tags.
link - This keyword will search for the sites, which have link to the specified site.
for example,
link:www.google.com
will search for sites, which have a link to the site www.google.com
related - This keyword will list all pages, which are similar to the specified web page.
info - This keyword will show information, that Google has about the specified website.
Well, that's all folks, I have included enough information in this post, that will be enough to search for password files, and break into servers, but always remember - Intelligence is a double edged sword. Which edge you end up using, is on to you.
Saturday, November 24, 2007
The magic cube

I've been trying to solve the Rubik's cube for quite some time now...
And finally, have got to a site, that gives a step by step, condition based algorithm for beginners. This is the Fredrich method, invented by Jessica Fredrich which is also the easiest method for cubing. Check the following link for the tutorial...
Original Post
Friday, November 16, 2007
traceroute made easy...

The traceroute applications, which have traditionally been used by hackers to trace the path to a certain computer, use UDP packets or ICMP echo request packets to that computer, by using a TTL of 1, and then incrementing the TTL value, so that the packet ultimately reaches the destination.
Here, I am going to explain how this works, for the newbies. The TTL value in IP packets, defines how long the lifetime is, in the network, during the transmission. It is called the Time To Live of the packet. Every computer that comes in the path of the packet, reduces the TTL value by 1, and forwards the packet to the next computer in the path. Thus, ultimately, the packet reaches the destination. But, if the packet has TTL, which does not suffice to reach the destination computer, the computer, which sets the TTL to zero, sends an ICMP time exceeded message(ICMP is used to communicate error messages in the Internet), to the sender computer, so that it can send another copy of the packet.
But unfortunately, in this world of firewalls, this method hardly works today, as the packets get filtered in the path, and the packet never reaches the destination. So, the trace remains incomplete.
But, fortunately, for the people like me, hackers have devised a new technique, with lesses chances of getting filtered, wherein a TCP packet is sent, with increasing TTL. So, the trace is not stopped in the middle, and the packets do trace the whole path for us.
TCPTRACEROUTE
Cracking the windows OS
Well, here comes the ophcrack live CD. The ophcrack has been the best windows password cracker, in the open source world till date, which utilizes rainbow tables, to crack windows password. Now, the ophcrack comes with a live CD, which runs a version of slackware, which is a sort of Linux, and then extracts the password hash, from the file, which stores the windows registry. Then, it cracks the password with the help of rainbow tables. I came to know about the live CD issue from another post in a blog. More the RAM of the computer, more is the crackable length of the password. Till now, it can crack passwords upto 14 characters, which is the maximum number of characters allowed in the password by windows. Yes, though the MD5 algorithm supports 128 characters long a password, but the windows front end limits the password to 14 characters.
So, windows is broken.....
Original post
ophcrack
Wednesday, November 14, 2007
Breaking into the ADSL router
Here in this article, I shall show you how I broke into someone's ADSL router, to change the password...
Step 1:
Scanning for the routers - In this step, I search for the systems in my network, which are also using ADSL routers as I am. I use a network scanner - nmap. A very popular port scanner, used worldwide by hackers and crackers, and which also featured, in the hacking part in Matrix reloaded. Alternatively, you can use your own custom built port scanner, if you do have the patience and will to delve into the world of network programming. This gives me a list of all the machines with open port number 23, which, in case of ADSL routers, is open. Additionally, these routers also have the port 80, the http port, open. So, we can access it with a web browser. I shall not give out the IP I broke into, due to security considerations. Let that be www.xxx.yy.zz. Surprisingly, it is one of the 233 routers, which I found, having the same username password pair, out of the 256 computers, that I scanned.
Another port scan on this particular computer reveals this:
C:\>nmap -p 1-100 www.xxx.yy.zzz
Starting Nmap 4.20 ( http://insecure.org ) at 2007-11-14 18:02 India Standard Time
Interesting ports on ABTS-mp-dynamic-zzz.yy.xxx.xxx.airtelbroadband.in (www.xxx.yy.zz):
Not shown: 97 filtered ports
PORT STATE SERVICE
21/tcp open ftp
23/tcp open telnet
80/tcp open http
Nmap finished: 1 IP address (1 host up) scanned in 62.340 seconds
C:\>
Step 2:
Breaking into the router - The default username and password are admin and password, in case of the Airtel ADSL routers, which is hardly changed by the users, after the installation of the router (also called modem in some places). The username password pair can be admin: admin or admin: r00t in other cases. So, all we have to do, is get to the router interface, and enter the default password and bingo, we got it - the access to the router.
This can be done in two ways, either through the telnet interface, that is found on the port number 23 or through the http interface, that is found on the port number 80.
In this article, I shall explain both the methods.
First, I'll explain the http interface method, the interface being authenticated by HTTP BASIC AUTHENTICATION. That means, when you type the IP in the address bar, a box pops up, which asks for username and password. After three failed trials, this box is gone, and a page displays, which says that you are not authenticated. So, here's how we do it.
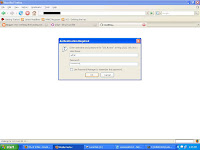 THIS SHOWS HOW I BYPASS THE PASSWORD DIALOG BOX
THIS SHOWS HOW I BYPASS THE PASSWORD DIALOG BOXAfter bypassing the security screen, I get to the main page.
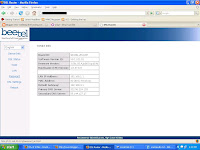
THIS IS THE MAIN SCREEN AFTER LOGIN. IT SHOWS ALL OPTIONS FOR INFO ABOUT THE PASSWORD RESETTING, ROUTER RESETTING, LAN SETTINGS, WAN SETTINGS AND DSL SETTINGS.
Then I change the password from the password reset page
This password, like a good old white hat, I reset back to what it was, after I was done. So, don't think I'm doing wrong stuffs.
Next, we delve deeper in this lake of ADSL router...
I then connect to the router, through the telnet interface. It means, I connect to the tcp port number 23, using a windows telnet client, called telnet. If you are using linux, then also, you'll be using this same command, as the command is same in all OSs. In the command prompt, I type :
TELNET WWW.XXX.YY.ZZ
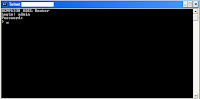
After this, I get the login screen, where I enter the default username and password to get access. Now, getting access to the telnet interface is like getting access to the router itself, which as a matter of fact, is a computer, with a version of linux embedded in it, in this case, and it will be so in most cases.
Now, I get to the prompt, that is, the router now waits for me to give commands. I type out help to see the list of available commands. As it is linux, commands are case sensitive. So, watch the case of the commands you give. The response follows:
> help
?
help
logout
reboot
adsl
atm
brctl
cat
df
dumpcfg
echo
ifconfig
kill
arp
defaultgateway
dhcpserver
dns
lan
passwd
ppp
remoteaccess
restoredefault
route
save
swversion
wan
ping
ps
pwd
sntp
sysinfo
tftp
>
So, here, we have the list of all the commands to use in this router. If I want too terminate any program running in the router, we use the kill command, the ping command will send ICMP echo signals to the IP in question. So, I use the ping command to find out the OS of the first computer connected to the network.
> ping 192.168.1.2
PING 192.168.1.2 (192.168.1.2): 56 data bytes
56 bytes from 192.168.1.2: icmp_seq=0 ttl=64 time=5.0 ms
56 bytes from 192.168.1.2: icmp_seq=1 ttl=64 time=0.0 ms
56 bytes from 192.168.1.2: icmp_seq=2 ttl=64 time=0.0 ms
56 bytes from 192.168.1.2: icmp_seq=3 ttl=64 time=0.0 ms
--- 192.168.1.2 ping statistics ---
4 packets transmitted, 4 packets received, 0% packet loss
round-trip min/avg/max = 0.0/1.2/5.0 ms
>
And we find that it's probably a linux OS, which is indicated by the ttl being 64. The case could also be, that the computer in question is using a firewall, which has modified the ttl to be 64. But that's a different topic. We check the other commands. The remoteaccess command lets you specify what services on the router are active.
> remoteaccess
Usage: remoteaccess
remoteaccess show [--service
remoteaccess --help
> remoteaccess show
remote access for FTP is enabled
remote access for HTTP is enabled
remote access for ICMP is enabled
remote access for SNMP is disabled
remote access for SSH is disabled
remote access for TELNET is enabled
remote access for TFTP is enabled
>
The passwd command is used to change the password, like in any *nix OS. The route command is used to access and/or modify the routing tables. cat is used to see what is written in the file, which is similar to the DOS command type. ifconfig is used to see the status of terminals connected to the router, like the ipconfig command in windows. sysinfo is used to get hardware information about the router.
> sysinfo
Number of processes: 24
8:08am up 8:08,
load average: 1 min:0.00, 5 min:0.00, 15 min:0.00
total used free shared buffers
Mem: 14248 13944 304 0 1084
Swap: 0 0 0
Total: 14248 13944 304
>
The ps command is used to see what all processes are running on the system.
> ps
PID Uid VmSize Stat Command
1 admin 252 S init
2 admin SW< [ksoftirqd/0]
3 admin SW< [events/0]
4 admin SW< [khelper]
5 admin SW< [kblockd/0]
6 admin SW [pdflush]
7 admin SW [pdflush]
8 admin SW [kswapd0]
9 admin SW< [aio/0]
10 admin SW [mtdblockd]
17 admin 296 S -sh
42 admin 896 S cfm
138 admin 196 S pvc2684d
230 admin 248 S dhcpd
240 admin 212 S bftpd
244 admin 216 S tftpd
247 admin 892 S telnetd
248 admin 1112 S httpd
252 admin 400 S pppd -c 1.32.1 -r Airtel -i nas_1_32 -u 07315064139_m
370 admin 200 S /bin/dnsprobe
403 admin 1176 S tr69c
2333 admin 924 S telnetd
2348 admin 268 S sh -c ps
2349 admin 260 R ps >
The swversion shows the software verion of the software running on the router.
> swversion
Usage: swversion show
swversion --help
> swversion show
3.06L.05.A2pB021g.d19d
>
The other commands, mostly deal with the configuration of the router, which I am not going to describe here.
Other than merely resetting password, crackers can also upload programs to this router, and can, thus monitor all incoming and outgoing traffic. Everything including email passwords, credit card numbers etc. can be watched. Rather than this, the username used to login is, in many cases stolen and sold on the Internet. Some years ago, such an incidence was reported in a national daily, that DataOne usernames and passwords were sold in Rapidshare for a Premium account, and the customers, were getting inflated bills, having no clue to how this was happening. So, users better beware.
Countermeasures
In order to avoid such attacks on privacy, all users must reset the password of their modems/routers, whatever they like to call it. For that, just type in 192.168.1.1 and give in the default username and password, which you can get in the modem's user manual. Then reset the password. Users better have the password well above 8 characters and include numbers and special characters as well, so that brute forcing becomes near to impossible.
This marks the end of this article.
NOTE: ALL THE INFORMATION GIVEN HERE, IS SOLELY FOR EDUCATIONAL PURPOSES. MISUSE OF THE INFORMATION GIVEN HERE WILL NOT BE THE AUTHOR'S RESPONSIBILITY.
About the ravaging of the Worldpay, a few years ago

This is the first headline, which made me know about the cyber crime scene, and thus, oriented me to the cyber crime scene stuff. A cool way to describe how the cyber payment giant was made to bite dust by a team of crackers. It is about the hacking scene in the year 2005.
Original Post
Email forging

Email forging has always been one of the easiest forms of email hacking ever used. It has been well known in the hacking community for quite a long time.
All one needs to know while forging email, is the basic knowledge of how the SMTP works. SMTP stands for Simple Mail Transfer Protocol - The protocol(set of instructions and rules) used to send email in the Internetwork. The total set of the step by step instructions from client to server can easily be found in any rfc database. Click here for the rfc relating to the SMTP. This link is for those, who are real PUJARIES of ultimate knowledge. Not for dummies...
A tutorial on how to forge email through any command prompt, can be very easily found in the Internet. So, I will not reinvent the wheel by redescribing the whole process here. The following link will show the simple tutorial on how to forge a simple email. Advanced email forging including attaching files in the mail will be posted soon in this blog. Keep checking.
The tutorial.
Tuesday, November 13, 2007
Free linux shipped at your doorstep...
Then came the Ubuntu linux, launched as a project by the company cannonical, who then launched four different versions of the award winning ubuntu linux, namely the UBUNTU, KUBUNTU, EDUBUNTU and EDUBUNTU. These linux are shipped to the door of any one who requests them, FREE OF ANY CHARGE. The XUBUNTU is not shipped at the time of this writing, due to lack of funds. Due to its free shipping feature, these distributions have become very popular worldwide. The UBUNTU uses a GNOME desktop environment, and the KUBUNTU uses KDE.
There is another very well known company in the linux market, which has later started a free meda project. The Redhat distribution, FEDORA is what I am talking about. It comes under the
Fedora free media program. Yes, FEDORA is also shipped for free. But due to some reasons, this one is at a halt this month.
There was also another Canadian website: thelinuxstore, which has been closed due to lack of enough funds. This site used to ship free distributions of various Linux brands, for free.
When we have to wait days for a free Linux distribution's download, these distributions can be shipped for free at your doorstep. The following links will lead you there...
The Fedora free media program
The Ubuntu linux
The Kubuntu linux
The edubuntu linux
Monday, November 12, 2007
Invincible Hacking

This is one of the most strengthening features of "Hacking" a.k.a. "The quest for knowledge", that has pursued me to land in this field. Hacking is unstoppable. One can only make it tougher for the hackers or crackers (whatever the case may be), but cannot in anyway, stop them. They will, definitely find their way out. I read about this first in a newspaper, when I didn't know anything about hacking. Readers, would definitely enjoy reading it...
Original post
Password cracking - The brute force method

The brute force method of password cracking, basically consists of generating every possible combination of all the characters that can be used in the password, and then encrypt each to be checked for a positive match with the original encrypted password.
The brute force method of password cracking, basically consists of generating every possible combination of all the characters that can be used in the password, and then encrypt each to be checked for a positive match with the original encrypted password. For example, if the encrypted password for my application is hyrulsjcl, and the original password be abcd(don't try this for my account... it's only a dummy example...). Then I try out all combinations, of all characters, in this case, lowercase alphanumeric characters, the combinations being: a, b, c, d, e, f.... z, aa, ab, ac, ad, ..... az, aaa, aab, aac, .... In this way, therewill be a positive ID for abcd, which will encrypt to hyulsjcl and password cracking will be complete.
One of the biggest shortcomings of this technique is that it is a very time taking process. Generating every possible combination, and then encrypting them takes a hell lot of time. As, we have to try out all possible combinations, the hackers had invented new hybrid technique for brute force, in which not every combination is tried out in sequence. Those password crackers, also termed smart brute force crackers check for the hash (the encryption) pattern, and then accordingly choose the next string to be matched for a positive ID.
So, here is a graphic description of how this all goes...
Brute force is not a very easy thing, when it comes to cracking real big passwords. But again, everything has its pros and cons...
a sample brute force cracker - It cracks passwords encrypted by DES, typically, a linux password is encrypted with the DES (Made by me of course ;-)).
a brute force string generator - It simply generates strings. It's got a fast algorithm. Lack of time led to not developing a cracker with it. Very soon, I'll upload that program. It will crack MD5 and DES passwords for linux.
NOTE: 1. You are downloading these files from: http://xtremehcl.googlepages.com The official website of HCl.
2. The original copy of this post is in the official HCl website's this page
Keep watching.....
Sunday, November 11, 2007
Password cracking - A brief intro to how they work and to bypass them...
Take any application, and it is probably very likely protected by some security measure (most likely a password). Passwords have become the most widely used, and one of the most dependable security measures in present cyber society. Take your email account. It is saved by a password. Your social account - may be in orkut or myspace or any other social network is protected by a password. Your own Operating system is probably password protected. Even your screen saver is protected by a password. Passwords are virtually everywhere. You simply cannot avoid them.
Since this blog is largely about bypassing these passwords, we shall first know how these passwords work. That is the very basis of all types of hacking and cracking.
So, let's end all the crap talk and jump to the real thing...
Passwords, are basically encrypted and stored in a separate file, which is checked, when authentication mechanism comes into play. The algorithm of encryption varies from system to system. In case of operating systems, it is stored in such a location where only the superior most user has access. In case of *nix platforms, it's the /etc/shadow or the /etc/passwd file. In case of windows NT, it's in the registry, or the SAM database. The passwords are encrypted using a predefined algorithm and then stored in these files. When the user has to be authenticated, the authentication program is run and the user has to enter the password, which is then encrypted to match with the already encrypted password present in the file. If it gives a positive ID the user is authenticated, otherwise, access is denied. In case of passwords in online accounts, the password may not be stored in the local computer. It is stored in the remote computer's password database. So, when you login to your computer, the password database used is (may be not in some cases, if your computer is a terminal to another server machine.) present in the local computer. In case of online accounts, as in the case of mail accounts, the password you enter is checked with the one in the server's database.
The very fact that the password is stored in a file in some storage media, is the vulnerability, that is exploited. All we have to do is get the file, and then crack the password. But again, we need to know the algorithm used to encrypt the password. "How to do that?" is the next question that comes in the mind. Fret not. The Internet has the answer to this. Once we get to know the algorithm, we can directly switch over to cracking the passw0rd. It is taken for granted that the reader knows programming. Even if the reader expertise any specific programming language's knowledge, still it is mandatory to learn C. It is the most powerful language I have come to know about, in the sense that it gives control over every single bit, in any memory location.
Now I shall tell about the various techniques of cracking passwords.
There are basically three different ways of cracking a password:
(1) Dictionary based cracking - Where we try out common passwords.
(2) Brute force cracking - Where we try all possible combinations of letters, numbers, and/or special characters.
(3) Rainbow tables - These are my favorite type of attack. It uses a database of preencrypted passwords, using a certain algorithm. This is used as a substitute to brute force, as brute force is a very tedious process, it takes a lot of time to crack a password. As the maximum amount of time is consumed in encryption of passwords, what we do is, encrypt the passwords, and store them in a database. When we have to crack a password, we have to do a simple lookup in the database. This makes the process real fast. The time consumption, thus becomes a one time affair - in the generation of these databases.
A more elaborate descriptions of these methods, along with sample programs is expected to be provided in a later post. Keep checking in...
So, what is hacking all about???
It's use has become so very restricted, that people have started taking the term for cyber criminals and computer vandals. But believe me, the very term hacking means "to redefine something to do what it was not made to do...". So, if you configure your FM radio, so that it can receive TV signals as well, it is hacking. If you sneak into someone's privacy, then we term it to be "cracking" not hacking. The very term hacking is clean.
We shall take some examples. All of us must have heard about the famous Operating system Linux. I'll tell you a truth associated with it. It was invented by a fin computer science student, whose name was Linus Torvalds. He was a hacker. Yes, a hacker. Hackers are not evil people. They are people in search of something. That something is knowledge. It is only their thirst for knowledge that makes them do what they do. So, from a broader aspect, even the black hat hackers, whom we call "crackers" aren't really bad people. They help us, the white hats. We are like family. They teach us that we have faults in the programs we have created, and that fault can be misused, and can be potentially harmful to people using the program.
The term hacker was first coined in the MIT(the Massachusetts Institute of Technology), for someone who was a computer expert. But, later on the media has corrupted the term, to designate computer criminals.
I shall now tell about the two major devisions in the world of hackers. There are, basically two types of hackers in this planet. The ones who like to use their knowledge in the positive side, whom we call the The white hats and the others, who use it in the negative side, whom we call The black hats. Always remember - intelligence acts as a double edged sword. The choice, which side you want to take is on to you. I'd say that none is "bad". Because the basic motive in either case is the same - freeing the civilization of ours, from all sorts of threats. To give us a wider view of this place, we are all living in.
This is all I have to say in the intro to hacking section.
A brief intro of mine...
I am not a white hat, and have been in the scene for above an year now...
I am a computer geek...
I am starting this blog to make people aware of all sorts of cyber threats in today's cyber world...
Basically, I am trying to form a basis of this "scene"
All I am trying to tell, is the truth...- The truth, about how safe we actually are...
Check out the official website : xtremehcl.googlepages.com to know more about my innovations and creations..
