Here in this article, I shall show you how I broke into someone's ADSL router, to change the password...
Step 1:
Scanning for the routers - In this step, I search for the systems in my network, which are also using ADSL routers as I am. I use a network scanner - nmap. A very popular port scanner, used worldwide by hackers and crackers, and which also featured, in the hacking part in Matrix reloaded. Alternatively, you can use your own custom built port scanner, if you do have the patience and will to delve into the world of network programming. This gives me a list of all the machines with open port number 23, which, in case of ADSL routers, is open. Additionally, these routers also have the port 80, the http port, open. So, we can access it with a web browser. I shall not give out the IP I broke into, due to security considerations. Let that be www.xxx.yy.zz. Surprisingly, it is one of the 233 routers, which I found, having the same username password pair, out of the 256 computers, that I scanned.
Another port scan on this particular computer reveals this:
C:\>nmap -p 1-100 www.xxx.yy.zzz
Starting Nmap 4.20 ( http://insecure.org ) at 2007-11-14 18:02 India Standard Time
Interesting ports on ABTS-mp-dynamic-zzz.yy.xxx.xxx.airtelbroadband.in (www.xxx.yy.zz):
Not shown: 97 filtered ports
PORT STATE SERVICE
21/tcp open ftp
23/tcp open telnet
80/tcp open http
Nmap finished: 1 IP address (1 host up) scanned in 62.340 seconds
C:\>
Step 2:
Breaking into the router - The default username and password are admin and password, in case of the Airtel ADSL routers, which is hardly changed by the users, after the installation of the router (also called modem in some places). The username password pair can be admin: admin or admin: r00t in other cases. So, all we have to do, is get to the router interface, and enter the default password and bingo, we got it - the access to the router.
This can be done in two ways, either through the telnet interface, that is found on the port number 23 or through the http interface, that is found on the port number 80.
In this article, I shall explain both the methods.
First, I'll explain the http interface method, the interface being authenticated by HTTP BASIC AUTHENTICATION. That means, when you type the IP in the address bar, a box pops up, which asks for username and password. After three failed trials, this box is gone, and a page displays, which says that you are not authenticated. So, here's how we do it.
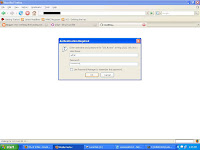 THIS SHOWS HOW I BYPASS THE PASSWORD DIALOG BOX
THIS SHOWS HOW I BYPASS THE PASSWORD DIALOG BOXAfter bypassing the security screen, I get to the main page.
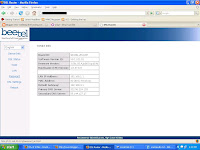
THIS IS THE MAIN SCREEN AFTER LOGIN. IT SHOWS ALL OPTIONS FOR INFO ABOUT THE PASSWORD RESETTING, ROUTER RESETTING, LAN SETTINGS, WAN SETTINGS AND DSL SETTINGS.
Then I change the password from the password reset page
This password, like a good old white hat, I reset back to what it was, after I was done. So, don't think I'm doing wrong stuffs.
Next, we delve deeper in this lake of ADSL router...
I then connect to the router, through the telnet interface. It means, I connect to the tcp port number 23, using a windows telnet client, called telnet. If you are using linux, then also, you'll be using this same command, as the command is same in all OSs. In the command prompt, I type :
TELNET WWW.XXX.YY.ZZ
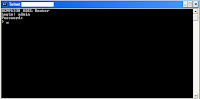
After this, I get the login screen, where I enter the default username and password to get access. Now, getting access to the telnet interface is like getting access to the router itself, which as a matter of fact, is a computer, with a version of linux embedded in it, in this case, and it will be so in most cases.
Now, I get to the prompt, that is, the router now waits for me to give commands. I type out help to see the list of available commands. As it is linux, commands are case sensitive. So, watch the case of the commands you give. The response follows:
> help
?
help
logout
reboot
adsl
atm
brctl
cat
df
dumpcfg
echo
ifconfig
kill
arp
defaultgateway
dhcpserver
dns
lan
passwd
ppp
remoteaccess
restoredefault
route
save
swversion
wan
ping
ps
pwd
sntp
sysinfo
tftp
>
So, here, we have the list of all the commands to use in this router. If I want too terminate any program running in the router, we use the kill command, the ping command will send ICMP echo signals to the IP in question. So, I use the ping command to find out the OS of the first computer connected to the network.
> ping 192.168.1.2
PING 192.168.1.2 (192.168.1.2): 56 data bytes
56 bytes from 192.168.1.2: icmp_seq=0 ttl=64 time=5.0 ms
56 bytes from 192.168.1.2: icmp_seq=1 ttl=64 time=0.0 ms
56 bytes from 192.168.1.2: icmp_seq=2 ttl=64 time=0.0 ms
56 bytes from 192.168.1.2: icmp_seq=3 ttl=64 time=0.0 ms
--- 192.168.1.2 ping statistics ---
4 packets transmitted, 4 packets received, 0% packet loss
round-trip min/avg/max = 0.0/1.2/5.0 ms
>
And we find that it's probably a linux OS, which is indicated by the ttl being 64. The case could also be, that the computer in question is using a firewall, which has modified the ttl to be 64. But that's a different topic. We check the other commands. The remoteaccess command lets you specify what services on the router are active.
> remoteaccess
Usage: remoteaccess
remoteaccess show [--service
remoteaccess --help
> remoteaccess show
remote access for FTP is enabled
remote access for HTTP is enabled
remote access for ICMP is enabled
remote access for SNMP is disabled
remote access for SSH is disabled
remote access for TELNET is enabled
remote access for TFTP is enabled
>
The passwd command is used to change the password, like in any *nix OS. The route command is used to access and/or modify the routing tables. cat is used to see what is written in the file, which is similar to the DOS command type. ifconfig is used to see the status of terminals connected to the router, like the ipconfig command in windows. sysinfo is used to get hardware information about the router.
> sysinfo
Number of processes: 24
8:08am up 8:08,
load average: 1 min:0.00, 5 min:0.00, 15 min:0.00
total used free shared buffers
Mem: 14248 13944 304 0 1084
Swap: 0 0 0
Total: 14248 13944 304
>
The ps command is used to see what all processes are running on the system.
> ps
PID Uid VmSize Stat Command
1 admin 252 S init
2 admin SW< [ksoftirqd/0]
3 admin SW< [events/0]
4 admin SW< [khelper]
5 admin SW< [kblockd/0]
6 admin SW [pdflush]
7 admin SW [pdflush]
8 admin SW [kswapd0]
9 admin SW< [aio/0]
10 admin SW [mtdblockd]
17 admin 296 S -sh
42 admin 896 S cfm
138 admin 196 S pvc2684d
230 admin 248 S dhcpd
240 admin 212 S bftpd
244 admin 216 S tftpd
247 admin 892 S telnetd
248 admin 1112 S httpd
252 admin 400 S pppd -c 1.32.1 -r Airtel -i nas_1_32 -u 07315064139_m
370 admin 200 S /bin/dnsprobe
403 admin 1176 S tr69c
2333 admin 924 S telnetd
2348 admin 268 S sh -c ps
2349 admin 260 R ps >
The swversion shows the software verion of the software running on the router.
> swversion
Usage: swversion show
swversion --help
> swversion show
3.06L.05.A2pB021g.d19d
>
The other commands, mostly deal with the configuration of the router, which I am not going to describe here.
Other than merely resetting password, crackers can also upload programs to this router, and can, thus monitor all incoming and outgoing traffic. Everything including email passwords, credit card numbers etc. can be watched. Rather than this, the username used to login is, in many cases stolen and sold on the Internet. Some years ago, such an incidence was reported in a national daily, that DataOne usernames and passwords were sold in Rapidshare for a Premium account, and the customers, were getting inflated bills, having no clue to how this was happening. So, users better beware.
Countermeasures
In order to avoid such attacks on privacy, all users must reset the password of their modems/routers, whatever they like to call it. For that, just type in 192.168.1.1 and give in the default username and password, which you can get in the modem's user manual. Then reset the password. Users better have the password well above 8 characters and include numbers and special characters as well, so that brute forcing becomes near to impossible.
This marks the end of this article.
NOTE: ALL THE INFORMATION GIVEN HERE, IS SOLELY FOR EDUCATIONAL PURPOSES. MISUSE OF THE INFORMATION GIVEN HERE WILL NOT BE THE AUTHOR'S RESPONSIBILITY.


1 comment:
Kewl!
Post a Comment